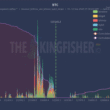
Nemo Protocol, a DeFi platform built on the Sui blockchain, was exploited for $2.4 million late Sunday, according to blockchain security firm PeckShield. The attacker targeted the protocol’s market pool shortly before scheduled maintenance, prompting the team to suspend smart contract activity while it investigates.
In a brief tweet, Nemo said a “security incident” impacted its market pool and that all Vault assets remain untouched. However, users in Discord and other community channels reported that vault balances were not visible after the exploit. The project has paused smart contract functions pending a forensic review and has not provided further public details.
The incident comes amid a difficult year for crypto security. Chainalysis’ 2025 Crypto Crime Mid-Year Update reports more than $2.17 billion stolen so far — already exceeding 2024’s total — with major incidents such as a record $1.5 billion ByBit breach accounting for a large share of losses. If current trends continue, Chainalysis warns losses could top $4 billion by year-end.
Community frustration has grown as moderators on Telegram and Discord went quiet and Nemo’s public information appears limited: the website lists few team details, a broken contact link, and a founder, Alex Yeung, with minimal online presence. That lack of transparency can slow user confidence and complicate recovery or remediation efforts.
What this means for users: exercise caution — avoid depositing funds to the protocol, monitor on-chain activity, and follow official channels for updates. Security incidents underscore persistent risks in DeFi, particularly with newer projects that offer limited public information.
Source: Decrypt. Read the original coverage for full details.